Introduction
On March 10, 2022, China Association of Automobile Manufacturers ("CAAM") released on its official website the Guidelines for Data Security Assessment of Intelligent Connected Vehicles (Draft for Comment) (the "Draft Guidelines"), which was prepared under the leadership of the China Industrial Control Systems Cyber Emergency Response Team and is seeking public comments until April 8, 2022.
The year 2021 is a critical year for data regulation. In terms of basic legislation, the Data Security Law and the Personal Information Protection Law have been successively issued and effective, forming the three pillars of data regulation together with the Cybersecurity Law. As for supporting regulations, the Regulations for the Security Protection of Critical Information Infrastructures, Administrative Regulations on Network Data Security (Draft for Comment), Measures for Security Assessment of Cross-border Data Transfer (Draft for Comment) and Practice Guide on Cybersecurity Standards — Guidelines for Classification and Grading of Network Data and other regulations have been continuously issued, providing important guidance and safeguards for the implementation of data compliance regulation. Meanwhile, in terms of vehicle data regulation, the Cyberspace Administration of China (“CAC”), the Ministry of Industry and Information Technology (“MIIT”) and the Information Security Standardization Technical Committee (“TC260”) have successively issued several documents, including the Several Provisions on the Administration of Vehicle Data Security (Trial), the Opinions of the Ministry of Industry and Information Technology on Strengthening the Admittance Administration of Intelligent Connected Vehicle Manufacturers and Products, the Guidelines for the Admittance Administration of Intelligent Connected Vehicle Manufacturers and Products, and the Information Security Technology — Security Requirements for Data Collected by Vehicles (Draft for Comment), reflecting a trend of strengthening regulation on vehicle data compliance and security.
In this context, the CAAM has formulated the Draft Guidelines based on the requirements of the aforementioned laws, regulations and standards. The Draft Guidelines are expected to provide guidance to intelligent connected vehicles-related enterprises when they conduct data security assessment on their own, and to provide a reference to competent regulators, third-party assessment institutions and other organizations when they organize supervision, inspection, administration and assessment of their collection and processing of data of intelligent connected vehicles-related enterprises as well.
To help enterprises quickly understand the Draft Guidelines, this article will provide quick Q&A ("Q&A") to clarify the core content of the Draft Guidelines.
Question 1: What is the scope of application of the Draft Guidelines (including the applicable subject and object) and what are the characteristics of such scope?
The Draft Guidelines apply to the internal data security evaluation made by intelligent connected vehicles ("ICV") enterprises themselves and at the same time provide a reference for competent departments, third-party evaluation agencies and other organizations to inspect, evaluate and supervise the ICV data security.
Under the above scope of application, the Draft Guidelines define "vehicle data", "general data", "personal information", "sensitive personal information" and "important data", the categories of data to be protected, and “vehicle data processor", the person to provide the protection.
In terms of categories of data to be protected, compared with the Several Provisions on the Administration of Vehicle Data Security (Trial) (the "Automobile Provisions"), effective as of October 1, 2021, the Draft Guidelines expand the scope of the "vehicle data" under the Automobile Provisions and add a concept of "general data" in addition to "personal information" and "important data". For details, please see the following figure:

Figure 1 Comparison of Definitions on "Vehicle Data"
From the perspective of the "vehicle data processor", as shown in the above figure, the term "vehicle data" in the Draft Guidelines is not limited to various types of data processed by ICV data processor, but rather the data processed by the "vehicle data processor". The Draft Guidelines define "vehicle data processor" as "any organization carrying out vehicle data processing activities, including automobile manufacturers, parts and software suppliers, dealers, repair agencies and travel service companies", which is significantly broader than ICV data processor.
According to the Norms on the Administration of Road Testing and Demonstration Application of Intelligent Connected Vehicles (for Trial Implementation) issued by the MIIT, "for the purpose of these Norms, 'intelligent connected vehicles' refer to the new generation automobiles that carry advanced vehicle-mounted sensors, controllers, actuators and other devices, integrate modern communications and network technologies, achieve intelligent information exchange and sharing between vehicles and others (including human beings, vehicles, roads, clouds, etc.), and are capable of sensing complex environment, making decisions intelligently and taking coordinated controls, which can offer a safe, efficient, comfortable and energy-saving driving experience and eventually replace manual operations. Intelligent connected vehicles are often dubbed as smart vehicles, self-driving vehicles, etc. Self-driving functions of intelligent connected vehicles are classified into three categories, namely the conditional self-driving, high-level self-driving and full self-driving.” In addition, according to the Taxonomy of Driving Automation for Vehicles (GB/T 40429 -2021), the driving automation is rated as Level 0 to Level 5, based on the degree to which the driving automation system is able to perform dynamic driving tasks, the allocation of roles in performing dynamic driving tasks, and whether there is any restriction on the operating scope, with the conditional automation, high-level automation and full automation corresponding to Level 3, Level 4 and Level 5, respectively. Given the above provisions, it can be understood that ICVs generally refer to vehicles that are capable of providing driving functions of Level III or above.
Question II: What types of data security assessments are regulated by the Draft Guidelines?
According to the Draft Guidelines, data security assessments for ICVs mainly include data security risk assessment, data security compliance assessment and security assessment for cross border data transfer. The Draft Guidelines mainly set out the implementation processes and assessment methods for data security risk assessment and data security compliance assessment for ICVs, and the security assessment for cross border data transfer shall be conducted by reference to subsequent laws and regulations and standards.
The following Q&A will provide further introduction to data security risk assessment and data security compliance assessment for ICVs. As for security assessment for cross border data transfer, the Automobile Provisions provide that "important data shall be stored within the territory of China in accordance with the law. Where it is necessary to transmit data abroad for business purposes, such data shall be subject to a security assessment organized by the national cyberspace administration authority in concert with the relevant departments of the State Council. Security management for data to be transmitted abroad involving personal information that is not included in the important data category shall be governed by the relevant provisions of laws and administrative regulations. " In October 2021, the CAC issued the Measures for Security Assessment of Cross-Border Data Transfer (Draft for Comment), and in the future, the security assessment for cross border data transfer of ICVs will refer to the officially effective version of the Measures.
Question III: What are the methodologies applied in the two types of data security assessment? Under what scenarios would the two types of assessment apply to?
The Draft Guidelines define two types of assessment: data security risk assessment and data security compliance assessment. `According to the Draft Guidelines, data security risk assessment refers to the process of assessing the security risks of an enterprise's data by analyzing the significance of, threats to, and vulnerability of digital assets, mainly disclosing the type, magnitude and probability of security risks. The data security compliance assessment refers to the process of judging whether data processing activities of ICVs are in compliance with the relevant laws, regulations, standards and management requirements and evaluating whether the enterprise's data security management measures are reasonable and effective, which focuses on reflecting the compliance of the data processing behavior with the relevant requirements.
From the perspective of assessment methodology, data security risk assessment applies risk analysis and assessment paths, with a similar methodology with that of Information Security Technology - Standards for the Assessment of Information Security Risks (GB/T 20984 -2007), Information Security Technology - Guidelines for the Implementation of Information Security Risks Assessment (GB/T 31509 -2015) and Information Security Technology - Guidelines for the Assessment of Personal Information Security Impact (GB/T 39335 -2020). However, data security compliance assessment focuses more on the approach of gap analysis, comparing the processor's current data processing practice with the compliance requirements of laws, regulations, policies and documents, to identify the processor's compliance level.
From the perspective of specific applicable scenarios, both data security risk assessment and data security compliance assessment can be applied to the whole business of the enterprise and various information systems relating to such business to be assessed and can also be an independent business and its related information system to be assessed. However, considering the different methodologies adopted by the two types of assessment, it is generally believed that the data security risk assessment is more applicable to the security risk assessment in data processing activities in a specific business scenario, such as the risk analysis in relation to data processing activities in a specific business scenario/need, while the data security compliance assessment is more applicable to the analysis of the overall data compliance of a company, such as the gap analysis in the overall data security level of a processor.
Issue IV: What are the differences and similarities between the implementation procedures of data security risk assessment and data security compliance assessment?
The Draft Guidelines contain detailed flowcharts for the implementation procedures of both data security risk assessment and data security compliance assessment, the details of which are as follows:

Figure 2 Flowchart for the Implementation of Data Security Risk Assessment Under the Draft Guidelines

Figure 3 Flowchart for the Implementation of Data Security Compliance Assessment Under the Draft Guidelines
Upon comparison of the implementation procedures of the two assessments, the main similarities and differences are as follows:
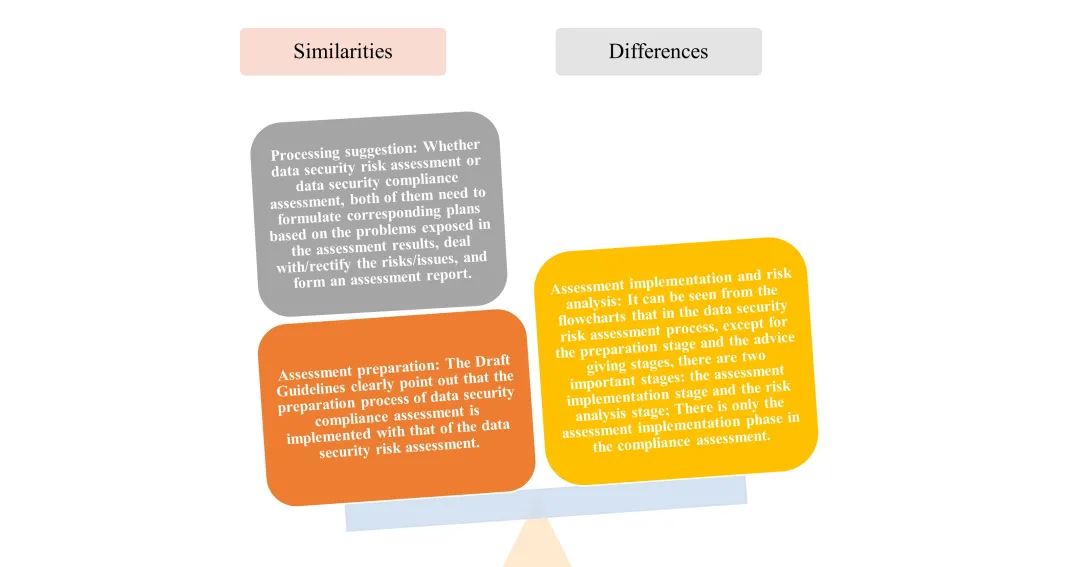
Figure 4 Similarities and Differences between Data Security Risk Assessment and Data Security Compliance Assessment Under the Draft Guidelines
Issue V: How to prepare for data security risk assessment and data security compliance assessment?
As mentioned in the previous question, the preparation phases for data security risk assessment and data security compliance assessment are basically the same, specifically speaking, the following steps can be summarized as follows: (1) determination of assessment targets → (2) determination of assessment scope → (3) formation of assessment team → (4) survey → (5) determination of assessment basis → (6) determination of assessment tool → (7) determination of assessment method. The key points for each step are summarized as follows:
Determination of assessment targets
● It can be all the business of the enterprise and various information systems related to business development to be assessed, or it can be an independent business and related information systems, etc.
● Output: assessment scope
Formation of assessment team
● Personnel composition: the management, legal, security, relevant business backbones, information technology and other personnel of the enterprise, together with external technical experts and technical backbones of relevant majors (when necessary), if necessary.
● Management measures: signing confidentiality agreements, clarifying the division of responsibilities, carrying out technical and confidentiality training, preparing emergency plans, etc.
● Output: List of members, roles and responsibilities
Survey
● Survey form: questionnaire survey, on-site interview, data review, etc.
● Survey content: data security management organizational structure, responsibilities and staffing; data security management related systems, processes and implementation; the network topology, authority control and security domain division of the information system related to the business to be assessed, etc.
● Output: survey report
Determination of assessment basis
● Basis: Applicable laws, regulations, and judicial interpretations; regulations and normative documents issued by CAC, MIIT and other relevant departments; existing international standards, national standards, industry standards, and group standards; data security, information security and other related security requirements
● Output: assessment basis
Determination of assessment tool
● Selection principles: comprehensive functions, timely update of monitoring rule base, no negative impact on data security, use of multiple evaluation tools
● Output: List of assessment tools
Determination of assessment method
● Program content: including risk assessment work framework, assessment team, assessment work plan, risk prevention, time schedule, project acceptance, etc.
● Output: Risk assessment plan
Issue VI: How to implement data security risk assessment?
The implementation of data security risk assessment is divided into three stages: data assets identification, data threats identification, and vulnerability identification. By means of assigning values to data assets, data threats and vulnerabilities, the Draft Guidelines quantify the basic data processing information possessed by processors, making it easier to conduct risk analysis and calculation in the next step.
(1)The identification of data assets can be attributed to the scope of data classification and grading work. According to the Data Security Law, China has established a system of classifying and grading data protection, providing for the protection of data in accordance with its category and grading, depending on the importance of data in economic and social development, and the degree of harm caused to national security, public interests or legitimate rights and interests of individuals and organizations in the case of data being falsified, destroyed, leaked, or illegally accessed or illegally used. The Practice Guide on Cybersecurity Standards — Guidelines for Classification and Grading of Network Data (the "Guidelines") to be issued by the TC260 in 2021 provides general guidance for the classification and grading of corporate data. The principles for the classification and grading of data are basically the same as those for the assignment and grading of data assets specified in the Draft Guidelines.
Table 1 Data Asset Value Assignment Table under the Draft Guidelines
Value | Identification | Object of Impact | Definition |
5 | Very high | National security and public interests | Once a data security incident occurs, it will have a serious impact on national security, social order, economic construction and public interests. |
4 | High | National security and public interests | Once a data security incident occurs, it will have a certain impact on national security, social order, economic construction, and public interests. |
Enterprise interests | Once a data security incident occurs, it will have a serious impact on enterprise business, reputation, and cause serious losses to enterprise assets. | ||
3 | Medium | Enterprise interests | Once a data security incident occurs, it will have a serious (relatively large) impact on enterprise business, reputation, and cause serious (relatively large) losses to enterprise assets. |
Personal interests | Once the personal sensitive data is leaked or illegally used, it will cause serious harm to the personal and property safety of personal data subjects. | ||
2 | Low | Enterprise interests | Once a data security incident occurs, it will have a limited impact on enterprise business, finance, and reputation. |
Personal interests | Once the personal non-sensitive data is leaked or illegally used, it will cause adverse effect to the personal data subjects. | ||
1 | Very low | Enterprise interests | Basically it has no impact on the enterprise. |
Personal interests | The relevant data cannot be traced to the personal data subject or is authorized to be disclosed by the personal data subject, and basically it has no impact on personal rights and interests. |
Table 2: Excerpts from Practice Guide on Cybersecurity Standards Guidelines for Classification and Grading of Network Data
Object of impact | Degree of impact | Reference description |
National security | Slight harm | 1. Causes slight impact on production, operation and economic interests in the region, the sector, and in related industries and fields 2. Impact is of short duration, causing limited impact on industry development, technological progress and industrial ecology, etc. |
No harm | No impact on national security | |
Public interests | Serious harm | Spreads to most areas of one or more provinces or cities, causing social unrest and having an extremely negative impact on economic construction |
General harm | Spreads to most areas of one or more prefectures, causing social panic and having a significant negative impact on economic construction | |
Slight harm | Spreads to a prefecture or part of the areas under the prefectural level, disturbs the social order, and has certain adverse impact on economic construction | |
No harm | No impact on public interests | |
Personal legitimate interests | Serious harm | The subject of personal information may be subject to significant, non-eliminable and insurmountable impacts, which are likely to cause damage to the personal dignity of a natural person or personal or property safety of a natural person is endangered, such as suffering from unaffordable debt, losing working ability, causing long-term mental or physical diseases, leading to death, etc. |
General harm | The subject of personal information may suffer from significant impact, it is difficult for the subject of personal information to overcome, and the cost to eliminate the impact is relatively high, such as fraud, funds embezzlement, blacklisting by banks, credit score damaged, reputation damaged, discrimination, dismissal, being summoned by court, deterioration of health, etc. | |
Slight harm | The subject of personal information may suffer from harassment, but such harassment can be overcome, such as paying additional costs, failure to use services that should be provided, causing misunderstanding, fear and tension, minor physical illnesses, etc. | |
No harm | There is no impact on the legitimate rights and interests of personal information or only a weak impact but can be ignored. | |
Organization legitimate interests | Serious harm | This may lead to severe penalties imposed by regulatory authorities (including cancellation of business qualification, long-term suspension of relevant business, etc.) or affect the normal operation of important/critical business, resulting in significant economic or technical losses and seriously undermining the reputation of the organization or leading to enterprises’ bankruptcy |
General harm | This may lead to punishment imposed by regulatory authorities (including suspension of business qualification or business for a period of time), or affect the normal operation of part of business, resulting in large economic or technical losses and undermining the reputation of the organization | |
Slight harm | This may lead to certain litigation incident, or part of business interruption at some time, causing slight damage to the economic interests, reputation, technology, etc. |
(2)As to the identification of data threats, the Draft Guidelines also use the method of assignment to score the potential threats to data in the whole life cycle of data processing (including collection, transmission, storage, sharing, use and destruction); the factors of value assignment mainly include the attack motivation, attack capability and the frequency of the data threat. Taking the threat frequency, for example, the Draft Guidelines classifies threat frequencies into five levels (very low, low, medium, high and very high) and provides specific criteria for their definition.
Table 3 Data Threat Frequency Assignment Table Under the Draft Guidelines
Level | Identification | Definition |
5 | Very high | Occurs very frequently (or ≥ 1 times/week); or is almost inevitable in most cases; or can be verifiably frequent. |
4 | High | Occurs frequently (or ≥ 1 times/month); or is very likely to occur in most cases; or can be verifiably frequent. |
3 | Medium | Occurs moderately frequently (or ≥ 1 times/half year); or is likely to occur in certain circumstances; or can be verified to have occurred in the past. |
2 | Low | Occurs infrequently (or ≥ 1 times/year). |
1 | Very low | Threats are almost impossible to occur. |
(3)With regard to data vulnerability identification, the Draft Guidelines classifies data vulnerability into technical vulnerability and managerial vulnerability. Examples of both can be found in the table below. The Draft Guidelines classify technical vulnerability into five levels, which are very low, low, medium, high and very high, according to the paths in which the vulnerability is exploited, the degree of difficulty for an attacker to exploit the vulnerability when accessing a target system, the level of identification requirements that the attacker needs to pass through in order to exploit the vulnerability, whether user interaction is required to make use of the vulnerability and other considerations. According to the impact on data confidentiality, integrity, availability and controllability of the vulnerability being successfully exploited, the severity of impacts is also classified as very low, low, medium, high and very high.
Table 4 Examples of Vulnerability Identification Content Under the Draft Guidelines
Type | Identification object | Identification content |
Technical vulnerability | Physical environment | It is identified from the aspects of machine room site, machine room fire prevention, machine room power supply and distribution, machine room anti-static, machine room grounding and lightning protection, electromagnetic protection, communication line protection, machine room area protection, machine room equipment management, etc. |
Network structure | It is identified from the aspects of network structure design, boundary protection, external access control policies, internal access control policies, network equipment security configuration, etc. | |
System software | It is identified from the aspects of patch installation, physical protection, user accounts, password policies, resource sharing, event auditing, access control, new system configuration, registry reinforcement, network security, system management, etc. | |
Application of middleware | It is identified from the aspects of agreement security, transaction integrity, data integrity, etc. | |
Application system | It is identified from the aspects of audit mechanism, audit storage, access control policies, data integrity, communication, authentication mechanisms, password protection, etc. | |
Managerial vulnerability | Technical management | It is identified from the aspects of physical and environmental security, communication and operation management, access control, system development and maintenance, business continuity, etc. |
Organizational management | It is identified from the aspects of security strategy, organizational security, asset classification and control, personnel security, and compliance, etc. |
After completing the identification of data assets, data threats and vulnerability, the Draft Guidelines provides the following risk analysis models and suggests that assessors calculate risk values by choosing the quantitative or qualitative calculation. Examples of risk calculation for quantitative calculation methods such as matrix method or multiplication method may refer to Information Security Technology - Information Security Risk Assessment Standards (GB/T20984-2007).

Figure 5 Models for Data Security Risk Analysis Under the Draft Guidelines
Issue VII: How to implement data security compliance assessment?
The implementation of data security compliance assessment mainly includes technology management assessment and data management assessment. For the former, the Draft Guidelines list contents in ten aspects, including the organisational structure, institutional framework, confirmation of the implementation of security compliance inspection, confirmation of the implementation of risk assessment, confirmation of the implementation of cross-border compliance, confirmation of the implementation of annual report, emergency response, personnel management, personnel training, and confirmation of the implementation of data preservation; while for the latter, the Draft Guidelines mainly provide the contents to be assessed in the whole life cycle of data processing, including the collection, transmission, storage, deletion, and other processes of data processing.
For the abovementioned two aspects, the Draft Guidelines set out specific safety requirements, evaluation methods and standards for determining the results. The determination standards of security requirement items and results can be regarded as a summary of various laws, regulations, and policy documents in respect of vehicle data processing compliance requirements. The Draft Guidelines provides a corresponding assessment method for each security requirement based on the specific security requirement. For example, to understand whether a data security management department has been established as required, the Draft Guidelines recommend that the work content and related documents of such department be assessed by means of document checking to confirm whether such department has performed its data security duties; and to understand personnel management and training, the Draft Guidelines require interviews with relevant personnel in addition to document checking so as to have a more comprehensive understanding of the company's operation. The above contents can provide very effective reference and guidance for vehicle data processors to establish internal data compliance system.
Table 5 Excerpts of Evaluation Contents of Staff Training Under the Draft Guidelines
No | Security Requirements | Assessment Method | Result Determination |
1 | Data security education and training for all employees shall be organized each year. | 1.Document Checking 2.Personnel Interviews | 1.Consulting the corporate data security training management measures and training plans, and confirming that the training contents including data security system requirements and practice specifications, such as laws and regulations, policies and standards, compliance assessment, technical protection, emergency response, knowledge and skills, security awareness, etc. 2.Consulting the training records and confirming that it has carried out offline centralized teaching, online training or other forms of education and training as required. Result Assessment: Compliance: satisfying the conditions set forth in Items 1 to 2 above. Non-compliance: failure to satisfy one or more of Items 1 to 2 above. |
Issue VIII: How to conduct data preservation and ensure the authenticity and completeness of data?
Regarding to the data security compliance assessment, the Draft Guidelines explicitly require that "confirmation of the implementation of data preservation" shall be conducted, and "on-site inspection" shall be adopted to ensure data collection under the principles of "no collection by default", "consistent data collection", "reliable data transmission", "data content and link encryption", "complete data transmission", and "desensitization".
According to the Draft Guidelines, the Draft Guidelines on Industrial Data Security Assessment sets forth requirements on the traceability system that ICV manufacturers shall use the data traceability system for data preservation to ensure the authenticity of data may be examined. The Draft Guidelines set out the detailed process for the storage and verification of data in the form of a diagram as follows: When an ICV uploads raw data collected within a certain period of time (including but not limited to contour processed video, images, vehicle operation data, and location and track data) to the manufacturer, the ICV shall synchronously calculate the hash value of the raw data and upload the same to the third-party data preservation platform, so as to ensure the traceability and verification of the manufacturer's data collection activities can be conducted.

Figure 6 Implementation Procedures for Data Preservation under the Draft Guidelines
According to the Draft Guidelines, for verifying the manufacturer's compliance with laws and regulations in the process of data collection, transmission, application and acceptance of inspections, and to ensure that the manufacturer does not collect excessive data, spread data or modify data, the manufacturer shall be subject to on-site data verification conducted by competent authorities and assessment institutions. The verification shall be based on data preservation, and relevant inspections and examinations shall be conducted in terms of data collection, transmission, storage and other activities to confirm the compliance, completeness and authenticity of the data submitted by the manufacturer.
On-site data verification refers to the sampling inspection conducted on the manufacturer's vehicles. During sampling inspections, it shall be ensured that samples, inspection time and period, and vehicle testing status are all random. The detailed principle of on-site data verification can be seen in the figure below.
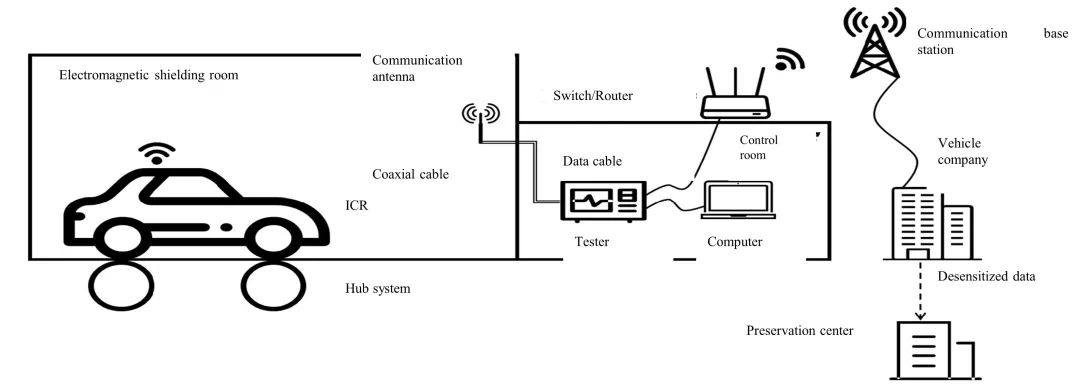
Figure 7 Testing Methods for On-Site Data Verification Under the Draft Guidelines
As shown in the above figure, the data (captured by the detection device) uploaded by the vehicle in the electromagnetic shielded room under the simulated scenarios such as the vehicle being charged and stationary, the vehicle being locked and powered off, and the vehicle being driven are detected by sampling. Hash calculation is performed on the data, and the hash value obtained by the calculation is compared with the hash certificate of the data synchronously uploaded to the certificate storage center at the vehicle end to confirm the accuracy of the hash value generation algorithm, so as to ensure that the hash value stored in the preservation center corresponds to the original data. At the same time, the original data captured by the detection equipment can also be used to analyze the compliance of the company's data collection, transmission and other activities.
Issue IV: What are the results of a data security assessment?
Regarding the results of the data security risk assessment, the Draft Guidelines divides the scores of the four indicators in Figure 5, namely likelihood of data threats (including motivation, capabilities and frequency of data threats), vulnerability availability, severity of vulnerability impacts and data materiality and their relevant sub-indicators into five levels: very low, low, medium, high and very high. Further, the Draft Guidelines provides high risk, medium risk and low risk assessment results based on the ratio of scores of each indicator as "very high", "high" and "medium". For details, please see the following table:
Table 6 Basis for Results of Data Security Risk Assessment Under the Draft Guidelines
Assessment conclusion | Basis for Judgment |
High Risk | With risk rating of "very high" accounting for more than 10% of the total risks, or with risk rating of "high" accounting for more than 30% of the total risks, such risk may be regarded as high. |
Medium Risk | With risk rating of "medium" accounting for more than 30% of the total risks, such risk may be regarded as medium. |
Low Risk | Where the risk rating of "very high" accounting for less than 10% of the total risks, the risk rating of "high" accounting for less than 30% of the total risks, and the risk rating of "medium" accounting for less than 30% of the total risks, the data security risk may be regarded as low. |
For the results of the data security compliance assessment, the Draft Guidelines provide the basis and calculation formula for the assessment results (see the table below). Among them, x is the score for each assessment item, from which it is 1 point if it is qualified, 0.5 points if it is basically qualified, and 0 points if it is not qualified; V is the score of the data security compliance assessment, and l is the number of data security compliance assessment items. Take "excellent" as an example. If there is no non-compliance with the requirements in the evaluation implementation process (that is, all the requirements are met or basically met), and the total score calculated by the calculation formula is above 90 points (inclusive), the enterprise can be recognized as excellent, and the enterprise only needs to make suggested rectification with regard to the assessment items that are basically met.
Table 7 Basis for Results of Data Security Compliance Assessment Under the Draft Guidelines
Assessment conclusion | Basis for assessment |
Excellent | If an assessed enterprise has no compliance items and the total score is 90 points or above, it will be regarded as excellent in data security level, and the enterprise may make suggested rectification with respect to the assessment items that are basically met. |
Good | If an assessed enterprise has no compliance items but some security problems and the total score is 80-89 points, it will be regarded as good in data security level, and the enterprise may make rectifications with respect to the relevant systems and rules that are basically met or not met. |
Qualified | If an assessed enterprise has no compliance items but a large number of security problems and the total score is 70-79 points, it will be regarded as qualified in data security level, and the enterprise may make rectifications with respect to the relevant systems and rules that are basically met or not met. |
Unqualified | If an assessed enterprise has any non-compliance item or has any serious security problem, which may lead to high security risk, for example, one or several items gets 0 or the total score is less than 70, it shall be considered as failing to meet the data security level requirement. The evaluated enterprise shall make compliance rectification according to the requirements of laws, regulations and relevant standards. |
The calculation method for the compliance assessment score is as follows:

Conclusion
As stated in the drafting background of the Draft Guidelines, with data becoming an important production factor, the automotive industry has entered the era of big data. As a highly digital product, ICVs need to collect a large amount of data both inside and outside the vehicle. The analysis and use of such data not only enhances the intelligence of automobile products, but also brings new challenges to data security. Therefore, how to minimize data processing risks and ensure compliance of data processing activities has become a problem that automobile data processors cannot avoid.
In this context, by issuing the Draft Guidelines, on the one hand, the CAAM intends to provide more practical guidelines for the construction of data compliance system of automobile data processors, on the other hand, it also reflects the CAAM's self-discipline attitude and trend of pioneering and piloting in the industries beyond the scope of formal regulatory regulations. In addition, although the Draft Guidelines is only a group standard and currently a draft for comments, it is possible that the Draft Guidelines will become an important reference for regulatory authorities in their law enforcement, since the main content of the Draft Guidelines is consistent with laws, regulations and rules, and the China Industrial Control Systems Cyber Emergency Response Team is also an important participating institution in the formulation of automobile data rules. In due course, it is possible that the Draft Guidelines be upgraded to a national standard or a regulatory document with a higher effective grade. Therefore, we recommend that vehicle data processing enterprises fully read the contents of the Draft Guidelines, pay close attention to the subsequent amendments and the coming into force of the Draft Guidelines. In addition, the enterprises may, based on their own practice, selectively incorporate the contents of the effective version of the Draft Guidelines into their own practice, so as to achieve safe and efficient use of vehicle data.
Annie Xue



Dr. XUE is a senior counsel supervising the compliance practice of GEN Law Firm. She specializes in regulatory affairs in cybersecurity and data protection, antitrust and anti-unfair competition, anti-commercial bribery, and Chinese social credit system. Dr. Xue has extensive experience in the said areas and profound understanding of the complicated issues standing at the intersection of those topics. Dr. Xue studied competition law at the College of Law of the University of Illinois at Urbana Champaign and obtained J.S.D. degree. She also participated in many research topics led by law enforcement authorities and academia as a postdoctoral fellow at the Institute of Law of the Chinese Academy of Social Sciences, and actively contributed to the formulation of competition and data regulatory policies. Before joining GEN, Dr. Xue served as a senior attorney in two Chinese law firms. She authored many articles and reviews related to legal compliance and served as an editor of The China Competition Bulletin hosted by Australia and New Zealand Government College.
CHEN Yang



CHEN Yang focuses on cyber security and data protection, personal information protection and compliance supervision consulting, and has participated in many difficult and complex cases. Yang has the Chinese lawyer qualification and is a Certified Information Privacy Professional (Europe) and Certified Information Privacy Manager by the International Association of Privacy Professionals (IAPP), having rich experience in the field of data protection.
LI Yuhang

LI Yuhang has provided legal services in portfolio management, administrative lawsuits, civil lawsuits, dispute resolution and enforcement on trademark, copyright, anti-unfair competition, IP and cyber security related areas for nearly 5 years. Mr. LI is especially experienced in trademark prosecution at home and abroad, and familiar with trademark litigation areas. Mr. LI also participates in many copyright infringement and unfair competition litigations for well-known multinational companies and network giants. Mr. LI has the Chinese lawyer qualification.










